Introduction
Open Source Software (OSS) has become essential to modern software development. OSS is incorporated into almost every electronic product, including cloud servers, personal computers, consumer electronics, automobiles, industrial equipment, and IoT equipment. Companies are required to develop products or services with high quality and faster time–to–market even under intense competition. They also have to keep up with the latest technology trends. OSS is indispensable in this pursuit.
It is not easy to answer precisely “What is OSS?”. Different people have different answers. However, most people would agree with the following: OSS is software for which the source code is provided. And the copyright holder allows others to use, inspect, modify, and share the software.
Linux is probably the most widely known example of Open Source Software. Linux Operating System is everywhere. It is incorporated into almost every major computing system, stock exchange servers, Internet servers, smartphones, electronics products, cars, and industrial equipment. Linux supports a large portion of the world’s core technological infrastructure.

Free but not Free of Risks
Legal and security risks are an integral part of any software, OSS is no different
Legal Risk is real
Litigation by an OSS copyright holder
It has occurred that failure to comply with the OSS license resulted in litigation against the user (and distributor) by the OSS copyright holders. In at least one case, a judgment required the defendant to suspend the shipment of their products containing OSS.
In December of 2009, there was a lawsuit related to Open Source software called “Busybox”. The Busybox program is widely incorporated into embedded systems and is licensed under the GPL version 2 license. In this case, 14
companies were the subject of the lawsuit, including some in the consumer electronics industry. The remarkable thing about this case was that companies suffered litigation on products that had been made by the Original Design Manufacturer.
In the past non-compliance issues were brought only by or on behalf of the OSS copyright holder, just like in the “Busybox” case, but OSS license enforcement is evolving…
Compliance failure as a defense claim
In some cases, OSS compliance issues have been raized in court as a defense claim. In August 2018 there was a lawsuit related to a commercial company in the wireless networking industry named Ubiquiti. Ubiquiti claimed a direct competitor, named Cambium, was using Ubiquiti’s firmware in violation of the Firmware License Agreement. Cambium responded alleging that the Ubiquiti products included code under the Open Source GNU General Public Licenses and Cambium’s own use of the portions of the Ubiquiti code subject to the GPL would not be an infringement. This case was settled on December 4, 2020, the full terms of the settlement are confidential.
OSS non-compliance claims by 3rd party
Not all OSS claims are raized by the copyright holder. In October 2021 the Software Freedom Conservancy (SFC) filed a lawsuit against TV vendor Vizio seeking to compel Vizio to comply with copyleft open source licensing requirements, including the obligation to make available source code. In this case, the SFC did not file the suit on behalf of a copyright holder of a particular open source project, but instead as the consumer of a product with open source components. This case is pending litigation.
Security Risk is real
OSS vulnerabilities are responsible for some of the largest data breaches known
OSS Vulnerabilities
Much like any other software, OSS may include unintended vulnerabilities that can be exploited by potential hackers.

Vulnerabilities in OSS are made public knowledge by contributors themselves, as well as by organizations like the Open Web Application Security Project (OWASP) and the National Vulnerability Database (NVD). OSS vulnerabilities are responsible for some of the largest data breaches known. In 2017 it was an open source vulnerability in the Apache Struts library responsible for the credit bureau Equifax breach. The bad actors exploited the Struts vulnerability to steal consumer credit data on 143 million U.S. consumers, nearly half of the entire US population. This perhaps constitutes the biggest leak in the history of the United States. According to the House Oversight Committee report, the Equifax breach was entirely preventable with basic open source security measures in place.
OSS Malicious code
Not all vulnerabilities in OSS are unintended. There are known cases of threat actors inserting malicious code into open-source libraries causing a ripple effect throughout the software supply chain. Every other project that uses code containing the malicious package suffers from the vulnerability created by the threat actors via the dependencies.
Supply chain issues
OSS compliance and safety cannot be achieved by one person acting alone.
As software becomes larger and more complex, the supply chain for software also tends to become larger and more complex. A modern software supply chain may include an OSS community, a software supplier, a semiconductor vendor that provides an SDK, and a final product vendor. If any member of a large and complex software supply chain fails to comply with license obligations, fails to provide the appropriate license information, or fails to provide a software clear of known exploitable vulnerabilities, it will cause a large impact to all downstream vendors who are obligated to comply with the license and may cause Irreparable damage to end-users who rely on the product safety.
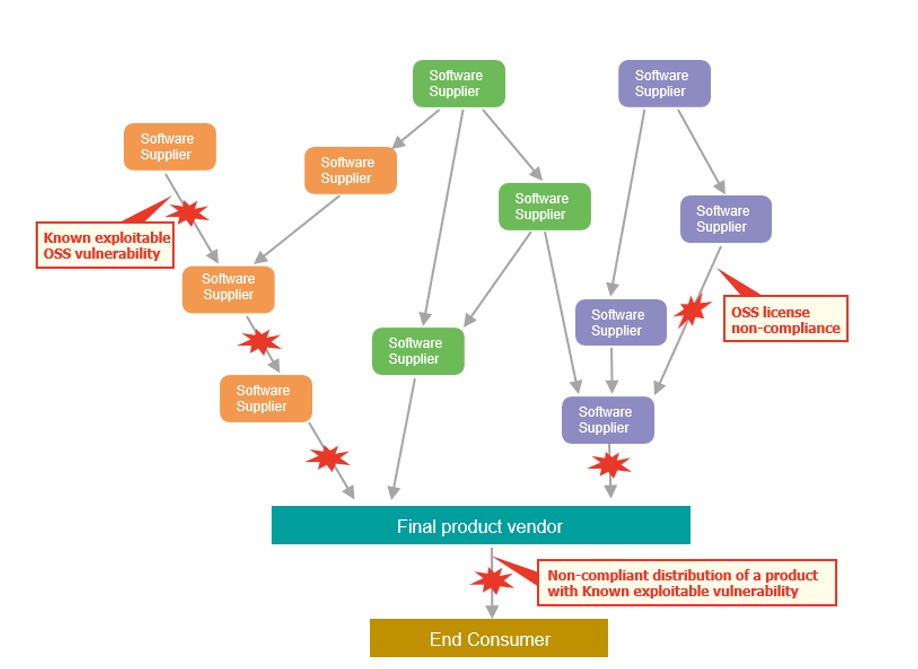
However, if software compliance and safety are managed appropriately in the upstream supply chain, these problems can be avoided.
Executive Order 14028
Cybersecurity in the software supply chain is a growing concern. In the United States and around the globe, businesses and organizations have experienced a number of high-profile and costly security attacks over the past few years.
In response to these high-profile security breaches and the ongoing need to enhance software security, U.S President Joe Biden issued an executive order in May 2021. The order seeks to improve the nation’s cybersecurity and has significant implications for U.S. companies and the open source community. Among the standards and requirements mentioned in section 4 of the executive order: (a) is the use of automated tools or processes to maintain the integrity of source code, and to check for known and potential vulnerabilities — and remediate them; (b) Maintain data about audits, the origin of software and components, and utilize secure software development practices, and (c) Ensure and attest to the integrity and provenance of open source software used within any portion of a product.
Federal Trade Commission
On December 9th, 2021 a serious vulnerability in the popular Java logging package, Log4j (CVE-2021-44228) was disclosed, posing a severe risk to millions of consumer products to enterprise software and web applications. This vulnerability is being widely exploited by a growing set of attackers.
On January 4th 2022, the Federal Trade Commission issued a warning it “intends to use its full legal authority to pursue companies that fail to take reasonable steps to protect consumer data from exposure as a result of Log4j, or similar known vulnerabilities in the future.”
The full outcome of Executive Order 14028 and the Federal Trade Commission warning is yet to be seen, but companies like Kaspersky have already announced they will release their software with full transparency of the Software bill of materials (SBOM) in a machine-readable form.
What you need to do to receive the benefits of OSS
When you choose OSS, functionality should be only one of the considerations
The Open Source software you use, and how you get it, can significantly impact the result. There are many important things to consider when selecting Open Source software. The type of OSS license, Security, and Community health are some of the additional aspects that should be considered.
Know your obligations
Almost all OSS licenses include some obligations that must be fulfilled, however, the conditions differ from license to license. Some licenses require only that a license notice and a copyright notice be included in the source publication. Other licenses require the disclosure of the source code and a written offer to obtain it. Some licenses have terms that affect what other OSS the first software may be used in combination with. A distributor is required to comply with all of the obligations defined in the license.
Ongoing Monitor for known vulnerabilities
An Open Source license will not change for a component already distributed, but new known vulnerabilities may be reported. Ongoing Monitor for new known vulnerabilities for all supported products is crucial for the safety of the end-users.
Manage your Open Source
The “rules of engagement” for using Open Source are usually defined in an Open Source policy. Without a clear policy in place, the risk of using open source will rise exponentially over time. On the contrary, a clear Open Source management strategy and policy will make day-to-day execution much more straightforward.